to vital infrastructure, affecting delivery of services and threatening public and environmental health and safety.
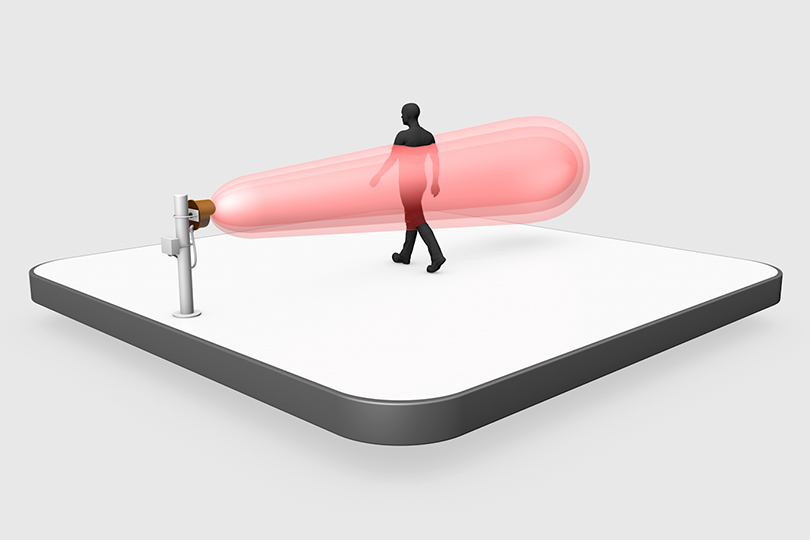
Providers within the electric and renewable energy, water & wastewater and oil & gas sectors rely on Southwest Microwave to protect their sites from acts of terrorism, sabotage, vandalism and theft, and against the legal and financial liability resulting from these attacks. Our technologies reliably prevent unauthorized access to property, critical equipment and networks.
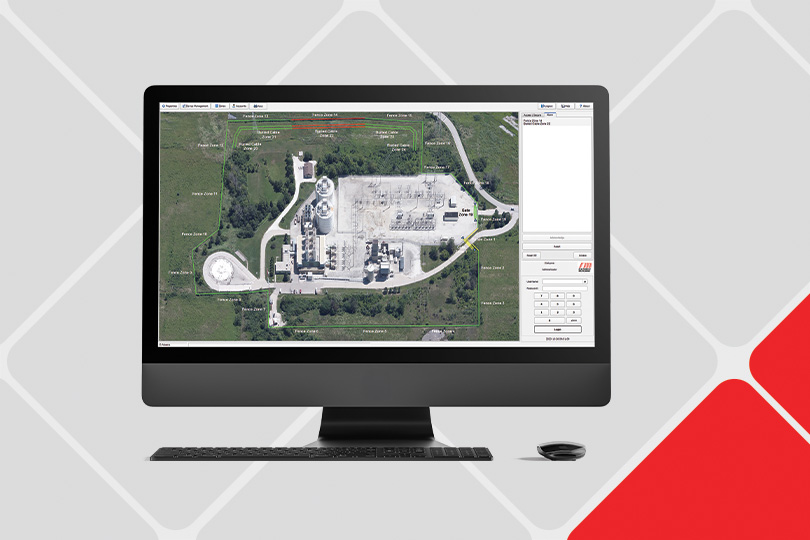
Our team understands the high stakes involved in securing power plants, substations, dams, control centers, treatment plants, pump sites, pipelines, tank farms, refineries, compression stations and storage facilities. Our conceptual designs are customized to address a site’s unique risks while also meeting the stringent industry standards and regulations required for utilities to effectively deter, detect, delay and assess security threats.